Malvertising: The Darker Side
In the post-COVID world, the rise of online businesses will be higher than ever. As a result, online networks will expand to reach larger online audiences. Malvertising is a cyber-threat that takes advantage of these pathways to reach the audience and uses them as a dangerous tool to steal personal and confidential data from its victims.
In organizations worldwide report-2019, it was found that 53% of organizations experienced a malvertising attack that led to at least a partial disruption of business operations. The number has only grown since the last 3 years and is nowhere to stop.
This post will take a closer look at Malvertising and how it can affect publishers. Let’s start with understanding Malware.
What is Malware?
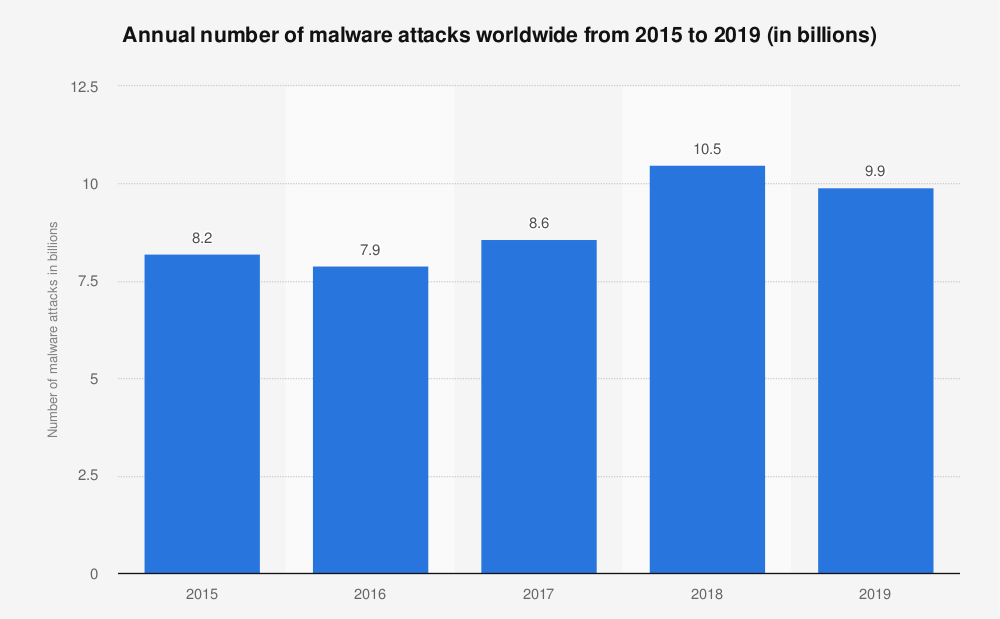
Malware is a condensed word for malicious software. It consists of code developed by cybercriminals to steal the data or gain unauthorized access to a network. The most common types of Malware are – viruses, spyware, adware, trojans, worms, and ransomware. The image below shows the number of malware attacks worldwide from 2015 to 2019.
What is Malvertising?
Malvertising is a word that blends Malware with advertising, in other words, malicious advertising. Cybercriminals use web advertisements to spread Malware. The ads are displayed on trustworthy websites, and these appear to be legitimate, but they have hidden codes, which redirect users to malicious websites or install Malware on their devices. User systems are attacked by either injecting malicious code into legitimate digital ads or creating fake advertisements and distributing them through ad networks. Attackers use Malvertising to:
- Commit identity theft
- Steal passwords and financial data
- Earn money through fake clicks in affiliate marketing
- Mine Cryptocurrencies
- Launch phishing scams
How does Malvertising work?
Here are several ways a cybercriminal can use to make you a victim of Malvertising. Below are two standard methods to target websites or browsers.
- An advertisement that tries to get the website visitor to click on it – Such ads tempt users to click on the link by displaying a fake message, “Your device is at risk” or “You have won a prize,” etc. Once the user clicks on the link, their system is infected by the malicious software.
- ‘Drive-by download’ – The infected ad is displayed on a legitimate website, and the ad pops up as the user visits this website. The user doesn’t need to click on the ad, but just loading the web page redirects the user to a malicious landing page that infects the user’s web browser or device by downloading the Malware into the user system.
How do attackers get their malicious code into ads?
Cyber attackers use several ways to insert malicious code into legitimate ads displayed on trustworthy websites and online platforms. We are mentioning the common ones below:
- Ad Calls: The ad networks push ads displayed on any website via third parties. One may be an attacker and can add malicious code in the advertisement.
- Post-click: When users click on an ad, they are redirected between several URLs before getting on the landing page. The attacker can compromise any of the URLs and execute malicious code.
- Ad creative: The ad creative is vulnerable, and Malware can be embedded in a text or banner ad.
- Pixel malware: Pixels send data to a server for tracking purposes. An attacker can intercept a pixel’s delivery path and send a malicious code response to the user’s browser.
- Video Ads: Video players are not protected against Malware and can infect users by displaying a malicious URL at the end of the video.
- Malware on a landing page: The users click on a legitimate ad, land on an actual landing page but are infected by a malicious on-page element.
How to prevent Malvertising?
The VPT Anti-malware Lab focuses on real-time monitoring and identifying malicious software for Windows & Mac Operating Systems. Our team of security researchers, malware hunters, data analysts, and software engineers are working to provide a dynamic response to famous, new, and unknown threats affecting Windows and MAC systems. For more information, write to us at – sales@viruspositive.com.
Visit our next Blog on 5 key aspects to consider before outsourcing a Software testing Service.